Understanding PIA and DPIA: A Legal Overview for Global Data Governance
In today’s data-driven environment, organizations are increasingly expected to manage not only technical and operational risks, but also legal and ethical implications of how personal data is collected, processed, and shared. Two critical tools in meeting these expectations are the Privacy Impact Assessment (PIA) and the Data Protection Impact Assessment (DPIA).
Both assessments are designed to help identify and mitigate risks to individuals’ privacy before launching new products, systems, or services. They are not merely compliance paperwork—they are proactive mechanisms for building trust, safeguarding data, and meeting obligations under privacy laws worldwide.
What Are PIA and DPIA?
PIA (Privacy Impact Assessment) is a structured process to identify and address privacy risks in new initiatives, especially where personal data is involved. It is generally considered a best practice in privacy governance frameworks.
DPIA (Data Protection Impact Assessment) is a legally required process under laws such as the EU’s GDPR when certain types of high-risk data processing activities are planned. Unlike a general PIA, a DPIA must follow specific documentation standards and content requirements set by law.
Although similar in intent, DPIAs are distinct in that they are often mandatory and subject to regulatory scrutiny.
When Is a DPIA Required?
Common scenarios requiring DPIAs include:
Processing of sensitive personal data (e.g., health, biometric)
Use of automated decision-making or profiling
Large-scale monitoring of public spaces
Cross-border data transfers
Implementation of AI systems or emerging technologies
Data processing involving vulnerable groups (e.g., minors)
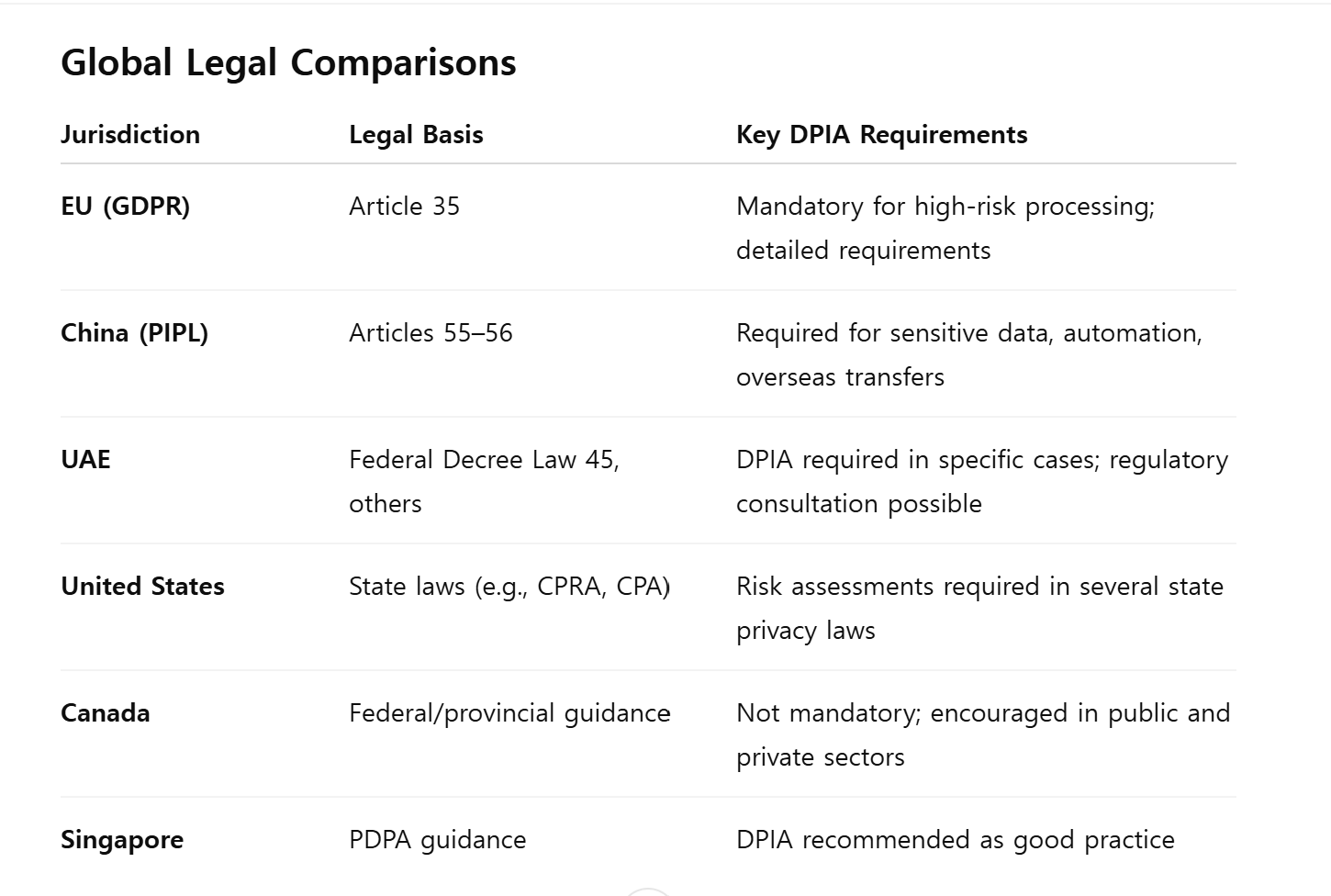
Global Legal Comparisons
Despite differences in terminology and format, the shared purpose across jurisdictions is clear: organizations must proactively assess risks and implement safeguards before engaging in personal data processing.
Practical Framework for Implementing DPIAs
Step 1: Threshold or Screening Assessment
Determine whether the planned data processing activity is likely to result in high risk to individuals' rights and freedoms.Step 2: Full DPIA Process
If risks are confirmed, conduct a detailed DPIA that includes:Description of data processing operations
Legal basis and purpose of processing
Risk assessment from the data subject’s perspective
Mitigation measures (technical and organizational safeguards)
Documentation of residual risk
Involvement of the data protection officer (DPO)
Consultation with supervisory authorities if risks remain high
DPIAs should be integrated early in the product or service lifecycle and updated periodically to reflect changes in processing activities or risk exposure.
Embedding PIA/DPIA into Organizational Practice
To ensure consistency and accountability, organizations should:
Embed privacy risk assessments into the design and approval workflow
Develop or adopt questionnaire templates for efficiency and legal consistency
Train internal stakeholders to identify and escalate data-related risks
Maintain comprehensive records of DPIA evaluations and outcomes
Periodically reassess DPIAs when processing changes
DPIAs are also an effective way to demonstrate “data protection by design and by default,” as required under Article 25 of the GDPR and reflected in many other global frameworks.
For organizations operating across jurisdictions or leveraging AI-driven tools, PIA and DPIA processes serve as essential components of a modern data governance strategy.
For more information or legal support regarding PIAs, DPIAs, or DPAs (Data Processing Agreements), please contact: sc@lexsoy.com
© LexSoy Legal LLC. All rights reserved.
This content is the property of LexSoy Legal LLC and is protected under applicable copyright and intellectual property laws.